Cloud migration has become a priority for many organizations seeking scalability, efficiency, and modernization, with 94% of enterprises already using Cloud services. However, as companies make the shift, they encounter significant data security and compliance challenges that must be addressed to protect sensitive information and reduce risks. With a data-centric approach, companies can prioritize data security at every stage of migration, effectively managing compliance and mitigating potential threats.
Cloud Migration: A Double-Edged Sword
Migrating to the Cloud offers clear benefits, including scalability, flexibility, and cost-efficiency. The ability to rapidly scale operations and respond to dynamic business needs is transformative.
- Scalability: Effortlessly adapt to changing needs by scaling resources up or down.
- Flexibility: Deploy applications and data on-demand, fostering agility and innovation.
- Cost-efficiency: Minimize hardware and software expenses with a pay-as-you-go model.
However, these advantages come with heightened security concerns:
- Data breaches: Sensitive information can be exposed if not properly protected during migration.
- Unauthorized access: Weak access controls can lead to unauthorized data access, compromising security.
- Regulatory compliance: Compliance with data protection regulations is essential but challenging in a Cloud environment.
Data-Centric Approach to Secure Cloud Migration
A data-centric approach prioritizes data security over system infrastructure. By focusing on data protection across its lifecycle (at rest, in transit, and during processing), organizations can ensure their Cloud environments remain secure and compliant.
Essential steps to implement a data-centric approach:
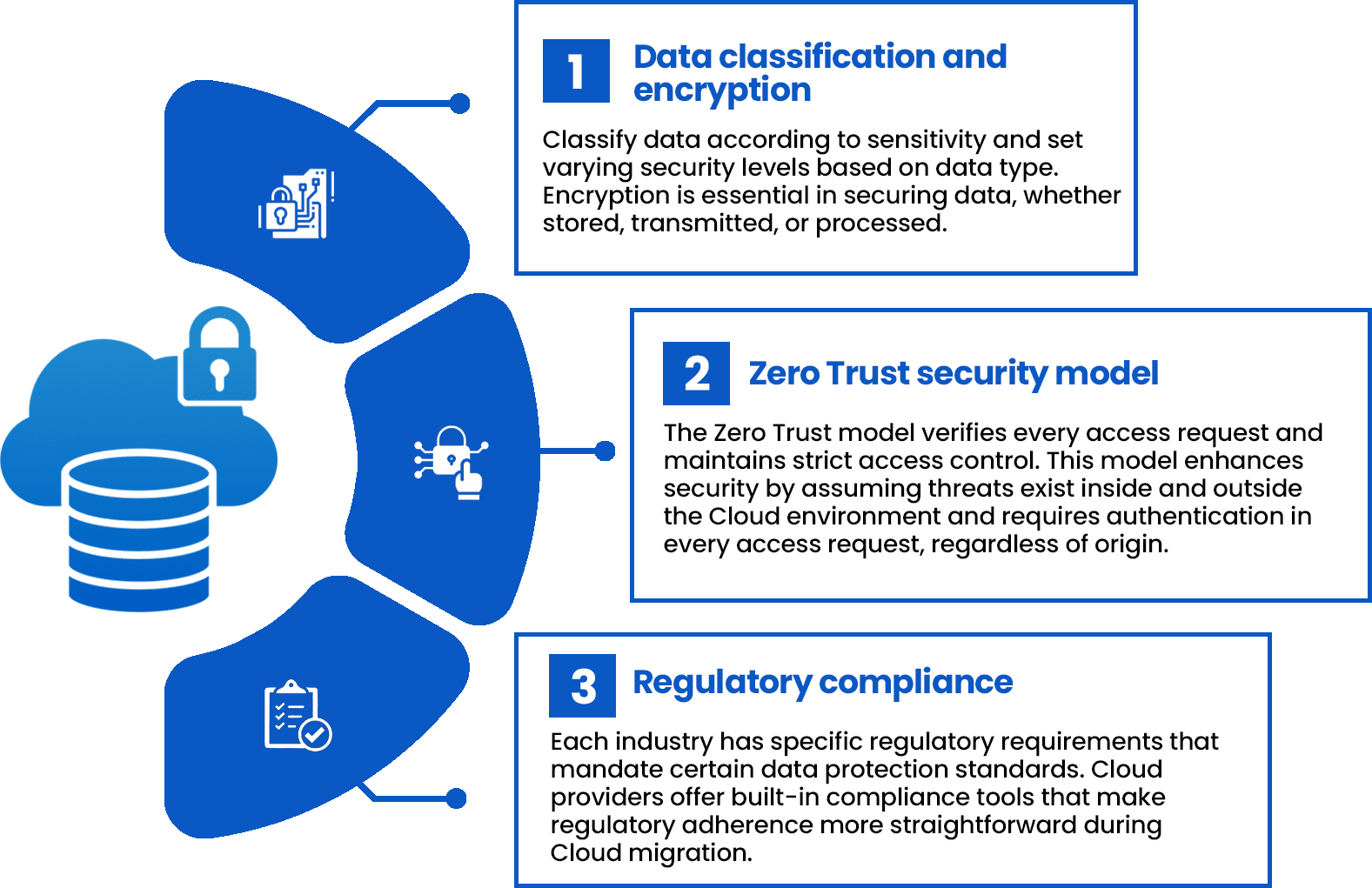
Continuous Monitoring and Security Assessment
The Cloud journey doesn’t end with migration. Continuous monitoring and threat assessment are vital to maintaining a secure Cloud environment. Implement security information and event management (SIEM) solutions to detect suspicious activity and potential breaches in real-time. Utilize AI-driven tools that analyze data patterns and proactively identify vulnerabilities, ensuring threats are found and mitigated before they impact operations.Up in the Secure Cloud
A responsible, data-centric approach ensures data security during Cloud migration. With a clear focus on protecting data across its lifecycle, organizations can create a Cloud environment that is both secure and compliant.
Taking the first step toward responsible Cloud migration doesn’t have to be overwhelming. Start by consulting with experts who can help design a data-centric Cloud migration strategy tailored to your company’s needs.
Don’t know where to start? Schedule a consultation with #StratpointCloud experts to explore how a secure, data-centric approach can transform your Cloud journey.




